With every webpage loaded, email sent, or video streamed, network traffic takes a complex journey…
Microsoft recently announced changes to Azure Active Directory. Today’s article covers the changes, providing sources for considerations, and how Exoprise’s service solutions will be affected.
What’s in a Name? The Old & New
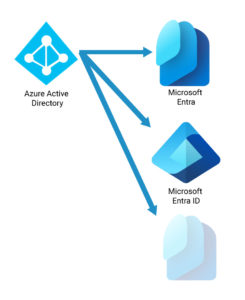
What’s changing? Microsoft is changing the product Azure Active Directory to Microsoft Entra ID, including its family of IAM (Identity Access Management). This includes re-branding current Azure AD products while adding several new ones including Microsoft Entra Verified ID, Microsoft Entra Permissions Management, Microsoft Entra Workload ID, Microsoft Entra Internet Access, and Microsoft Entra Private Access. This does not include Windows Server Active Directory, the on-premises LDAP framework. For more information, see Microsoft’s announcement.
For additional details about the fundamentals, see this discussion.
Why The Name Change for Microsoft Entra ID?
Microsoft wanted to delineate between Azure AD and the new SASE family of products from existing products in the Azure platform and the more traditional Windows Server Active Directory. The name change for Azure Active Directory (Azure AD) to Entra ID allows for a clearer distinction. Microsoft wanted to rebrand, extend and build upon the entire Microsoft Identity Platform.
Here’s more from Microsoft: “Today we’d also like to highlight other innovations in the Microsoft Entra portfolio that strengthen defenses against attackers who are becoming more adept at exploiting identity-related vulnerabilities such as weak credentials, misconfigurations, and excessive access permissions.”
Additionally, Microsoft has been concerned with achieving higher security standards with decentralized identity, access, and management as well as improving employee user experience as noted in the following quotes:
“According to Forrester research from 2022, 60% of business and technology professionals indicated that improving the experience of employees was a key IT objective during the next 12 months. 8 Relatedly, interviewees said that a primary goal for their organizations was to improve user experience (UX) by enabling SSO for all applications and from any device or location. Interviewees recognized that users who did not have to enter their credentials at every step were more productive and that a poor sign-on experience is not only frustrating for end users but also negatively impacts how the organizations perceive their IT and identity teams. “
Follow this link for a study of the ROI for the new Microsoft Entra family of products commissioned by Microsoft.
Improved Efficiencies from SASE and IAM
Microsoft has collaborated with the Identity and Access Management (IAM) community to tackle various challenges related to identity and access management, resulting in significant cost reductions. By addressing several factors and issues, Microsoft has successfully achieved efficiencies and cost savings, including:
- Reduction of legacy infrastructure and the replacement of previous IAM solutions.
- Significant increases in the efficiency of IAM teams, which translates into faster response times and improved overall performance.
- Reduction of security breaches by strengthening security measures such as improving ID, password, and permission policies.
- Faster time to grant access to resources, which increases product development velocity, through accelerated provisioning of access rights.
- Self-service solutions have led to a significant reduction in password reset requests, saving valuable time and resources for both end users and IAM teams.
- Seamless access through Single Sign On (SSO) to resources and streamlined user experiences resulted in hours of increased productivity for business end users.
- Ensured regulatory compliance, which reduces potential penalties or legal risks but also enhances trust and confidence among customers and partners.
- Flexibility and enhanced security and access control through conditional access
- Improved IAM efficiency has established smoother workflows and improved collaboration with its partners, resulting in reduced complexities and increased efficiency.
What Isn’t Changing?
Current Azure AD functions are not changing, just the branding. Additionally, the enterprise on-premises pieces, Active Directory (AD), are not changing, nor is the Azure platform. It’s important to note that Azure Active Directory has never actually been part of either Azure or the traditional Active Directory platforms. View this linked page for a full list of Microsoft products and how they are affected by the Azure AD branding change to Entra ID.
Microsoft Entra ID Future Products
- I’m using SASE and IAM products, which work well. How will Microsoft Entra ID affect other SASE & IAM platforms? The primary players in this market are Palo Alto Networks and Zscaler, along with a few other vendors. According to this article, Microsoft is already operating with overlap between the two:
“First, you have to start with the fact that Microsoft and Zscaler have a significant tech partnership themselves. While they could throw that away, in the complex world we live in, there is still value in their collaboration for both parties. There are a number of integrations between both products that seek to enrich each other’s ecosystems and to provide security admins already overwhelmed with tools, a slightly simpler world. We increasingly see companies that welcome ecosystem plays rather than build monopolies as being more successful.”
Additionally, as noted in this initial review, the new SASE solution for Microsoft currently accepts Microsoft 365 tunneling. Existing solutions can continue to run beside this new product. Exoprise will continue to support monitoring apps over these existing SASE solutions. Our CloudReady synthetics fully test Entra ID Single Sign-on, tunneling and proxying through Zscaler and Palo Alto and will do so for Microsoft products. Exoprise Service Watch detects, automatically, when using any of the tunneling technologies and can detect network slowdowns in real-time for end-users.
How is Exoprise positioned to address this change with its products?
With the coming branding, and more importantly, product changes behind Microsoft Entra ID, Exoprise has Azure AD sensors that synthetically monitor the service, 24/7, to detect changes and performance issues. Watch this short video for an idea of how quickly our Azure AD sensors detect outags and problems.

Historically, Microsoft’s identity and access solution, AAD now Entra ID, has been the source of outages and performance issues within the Microsoft ecosystem (or platform, etc.). As the cornerstone of Microsoft’s identity, permissions, authentication, and control for all things Microsoft and Azure, the dependencies on this critical infrastructure are considerable. Every customer should ensure that they have insight into what’s being changed and how its resilience might affect their own deployments.
Here are a couple of examples of upcoming Entra ID updates:
- IPv6 enablement for Azure AD: Microsoft Entra ID will be needed. This change means large consequences for customers’ network access to Entra ID. Depending on SDWAN and network conditions (which should be tested before implementation), access to AAD can be affected.
- MFA changes: Microsoft has numerous enhancements on the roadmap for MFA. Exoprise supports testing Microsoft 365 MFA through most of its sensors, and there have been a number of MFA related outages.
What changes will be required by Exoprise?
Currently, there are no changes required to monitor Microsoft Entra ID. Existing Azure Active Directory sensors (one of our most popular) continue to operate as is. Over time, as the product set for Entra ID expands, Exoprise will introduce new monitoring for vital pieces of Entra ID infrastructure.
Will there be a software update?
Since Exoprise products are software-as-a-service (SaaS), there is no need for customer-side updates. Everything is updated automatically from the service, including sites and sensors.
Conclusion
In closing, technical changes are a constant factor in the world of computing, especially for businesses. Every organization must be cognizant of all updates from every computing, network, cloud, and security provider. As both a Microsoft Partner and an independent Software Vendor (ISV), Exoprise stands ready to provide pertinent monitoring discovery and assessments combined with fine-tuning of all network resources at every level, whether SASE or on-premises.